Multi-factor Authentication
Multifactor authentication, or MFA, is an authentication method that requires at least two out of the three types of items:
- Something you know, like your password
- Something you have, like your phone with an authentication app or like a physical key such as a YubiKey
- Something you are, like your fingerprint, face, voice, or other biometric piece of information
MFA builds in another layer of protection in the authentication process by requiring more than one item in the above list. People have a tendency to reuse passwords or to use weak passwords for both personal and work accounts. It’s easy to crack into a system when someone reuses a password from an account that was breached and the password data subsequently posted or sold online. When combined with two-factor authentication (2FA), a compromised reused password is less likely to allow access to other systems.
What is 2fa?
Two factor authentication (2fa) is an authentication method utilising two of these factors. In the case of trentend this is something you know (your password) and something you have (your phone or computer).
Your password you are already familiar with, you may be less familiar with something you have using an authenticator app. We will look at that here.
Something you have
You have a phone, or a computer. How can you prove to a service that you want to access (in this case talkback), that not only is it you from your password, but also it is even more likely to be you because you have your phone?
It turns out that this is deceptively simple, and secure.
You register a piece of software, an authenticator, on your device, with the service in question. This involves sharing a secret (in the form of a qrcode, or a string of apparently random characters). The service knows the secret that it has shared with you, and can use a specific algorithm to produce time limited codes by running this secret through the algorithm. The authenticator, on your phone or computer, uses the same algorithm, and the same shared secret, to independently produce exactly the same time limited codes. The algorithm everybody knows, but without the specific secret nobody else can generate the identical codes. So when you enter the correct code, the service knows that you have the device that you registered with the service. It does this without transmitting any information anywhere (except your process for entering the code into the service). It cannot be intercepted, and if someone sees you entering a code it doesn't much matter. In 30 seconds it will no longer work to authenticate you with that service.
An Authenticator
Is a mechanism to provide a code to demonstrate the something I have without the possibility of compromising it. That is it is a no traffic code generation method. The authenticator app on your phone or computer is linked to the authentication provider (in this specific case turnstile.trentend.uk). Then on request it can be used to generate a code, know to the authentication provider. This code changes every 30 seconds, and is highly resilient to brute force cracking. This is the basis for a one time pad (OTP). The code happens one time, and for a limited time period, and is not easily guessable. Prior knowledge of previous codes does not help cracking the code. It happens only one time.
The google authenticator is perhaps the most widely known and used authenticator, and the instructions for it's use follow at the end of this article. Those instruction also serve as broadly generic instructions for other authenticators. The process is much the same whatever you choose to use.
Android authenticator
There are many authenticators available for android. I recommend aegis. You can protect your OTP's with a password (or biometric security, if your phone supports it). You can export an encrypted backup (opened with your password). I use this as my device of choice.
Linux Authenticator
Yeah, niche I know. But aegis exports an encrypted json backup, that can be imported into mauborgne. So I can capture qrcodes on my phone, and export them to my computer. Which is right handy.
Windows Authenticator
I haven't used it, right. But 2fast seems to tick a lot of boxes. It's open source, free, with a decent feature set, and the roadmap and github activity suggests it's heading the right way. So if I was using windows, I would probably try 2fast.
Google Authenticator
Is a widely known and used authenticator, available for iPhone, iPad, and Android devices. You can have it on iOS, iPadOS, and Android if you really want.
You do not need a Google Account for this. While you can obviously use it with Google's system you can still use it with other third-party services without linking your Google Account to the authenticator.
Given that the system relies on you either entering a set-up key or scanning a QR code, it is highly advised to set up the 2FA on a different device than the one you're setting up Google Authenticator on.
How to set up Google Authenticator for iPhone and iPad
- Download Google Authenticator from the App Store to your device. It is free to download.
- Sign into whatever service you want to enable 2FA for, and attempt to set it up. This could be an option in account settings under a section marked "security" and an option offering to "set up two-factor authentication," for example, but this will vary between services.
- When asked, you should select to use an authenticator app. You may be recommended to use specific authenticator app, so check that Google Authenticator is on that list.
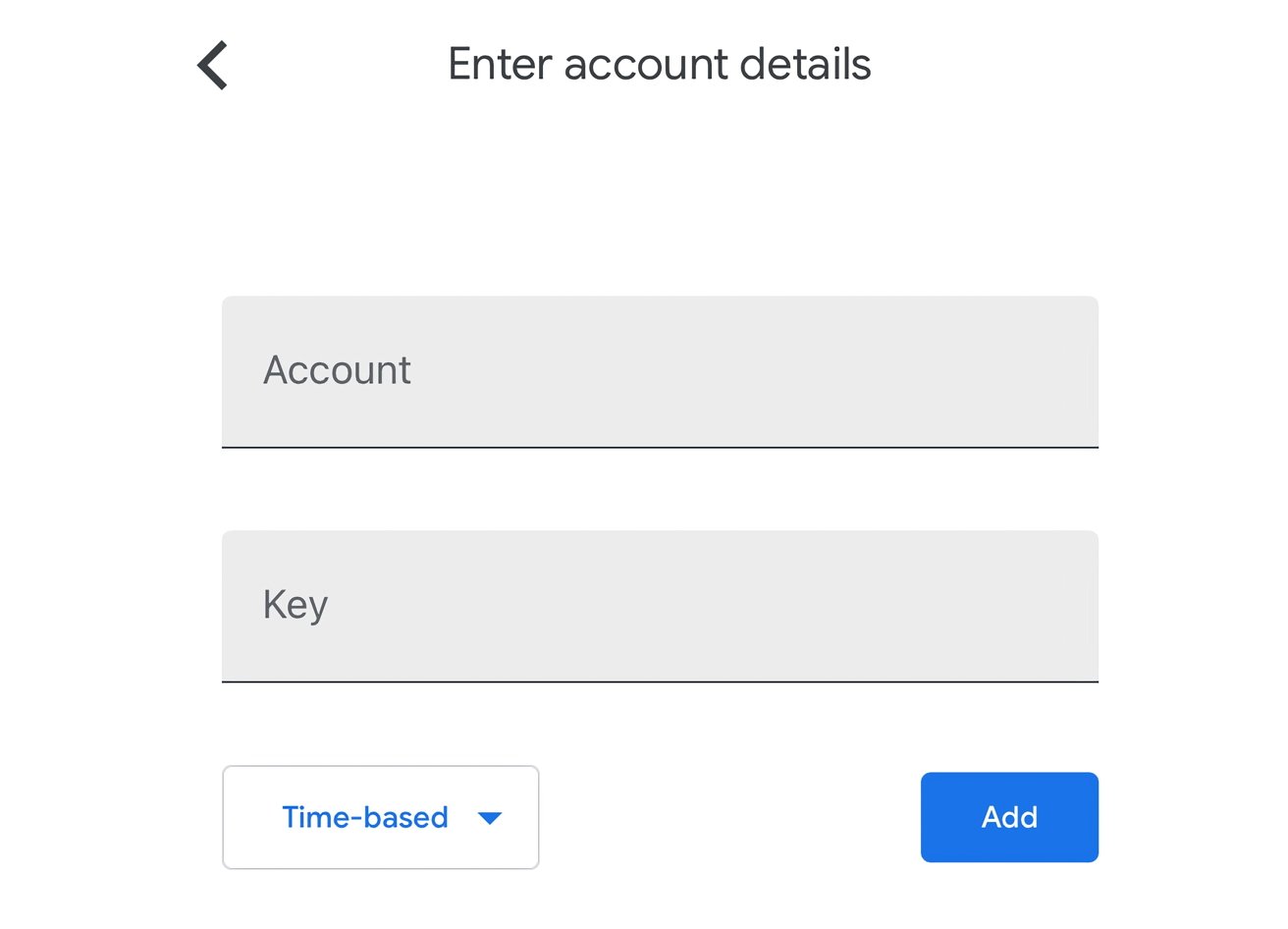
- Once presented with either a QR code or an authenticator key, open Google Authenticator on your iPhone or iPad.
- If this is your first addition to the app, you will be asked how you want to add the code directly. Otherwise, select the plus symbol in the bottom-right of the screen.
- If a QR code is presented to you in the site or app you're setting up 2FA for, select Scan a QR Code, then use your device's camera to scan the code.
- If a key is offered, enter in the account name (usually the relevant email address) and the key provided to you on-screen. Make sure to select whether it is Time-based or Counter-based if the account system advises as such, otherwise leave it to Time-based.
- You will then be asked to confirm that the authentication system has worked. Enter the six-digit code appearing on your device's screen into the app or service you're setting 2FA with as confirmation.
Once you're set up, you will be asked to use the authenticator app to generate a code to log into services, whenever you log in.
This is straightforward, as all you need to do is open Google Authenticator, look for the service and account name relating to it, and then read the associated six-digit code. Since the code changes periodically, you may want to wait until the timer expires and a new code appears, to maximize your code entry time.
You can enter the security details manually, but a QR code is quicker.
If you're entering the code into an app on the same device, tap the code to copy it to the clipboard, which you can then paste into the app's textbox for entry.
How to delete account listings from Google Authenticator for iOS
- Open the app and tap the three dots in the top right.
- Tap Edit.
- Tap the pencil icon next to the relevant account.
- Tap the trashcan.
- On the confirmation box, tap Remove account.
Remember that removing an account from the Google Authenticator app doesn't affect the status of 2FA on the account itself. If you wish to remove 2FA from the account, do so before removing the Google Authenticator listing.
Any old iron
There are many different authenticators than are mentioned here. You may need to exercise your judgement and research alternatives if you wish to use one. There are reports of rogue applications that have been found to expose secrets. The authenticators that are mentioned here fall into two categories:
1. Open source, where the application can be shown to have been built from the open source code, and the open source code provides no known mechanism to expose your secret.
2. Google authenticator, which can be subject to no such scrutiny, but is relatively ubiquitous, and those appley chappies need something that 'just works'.